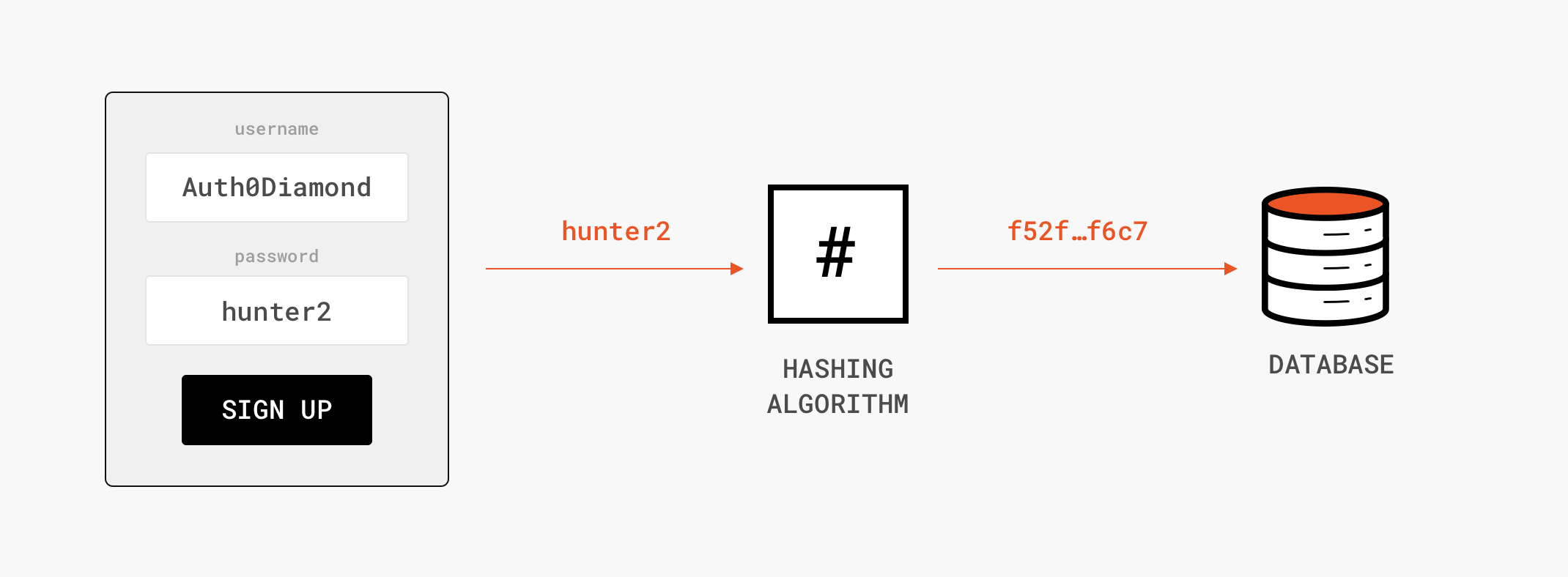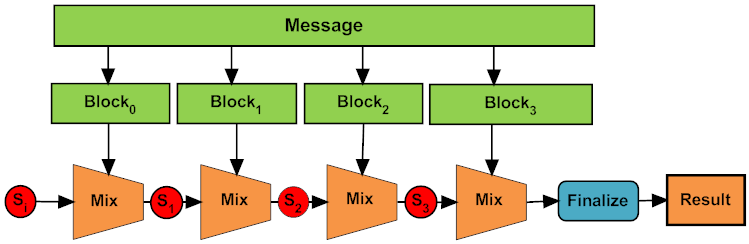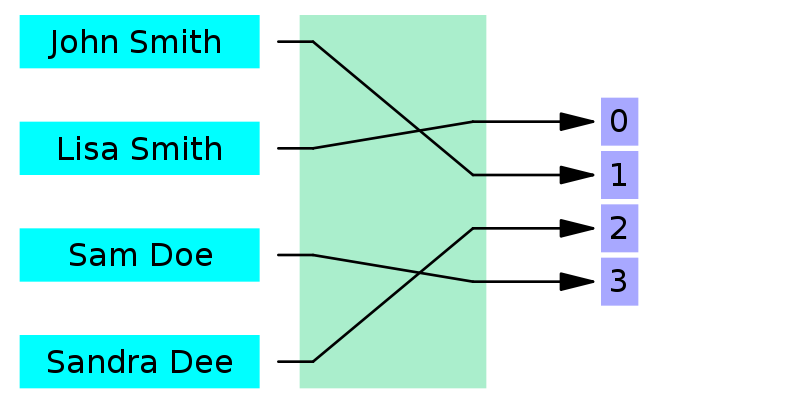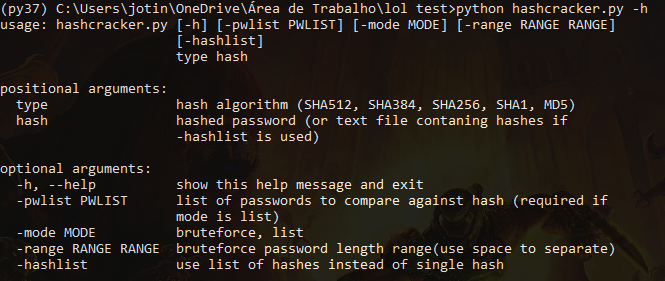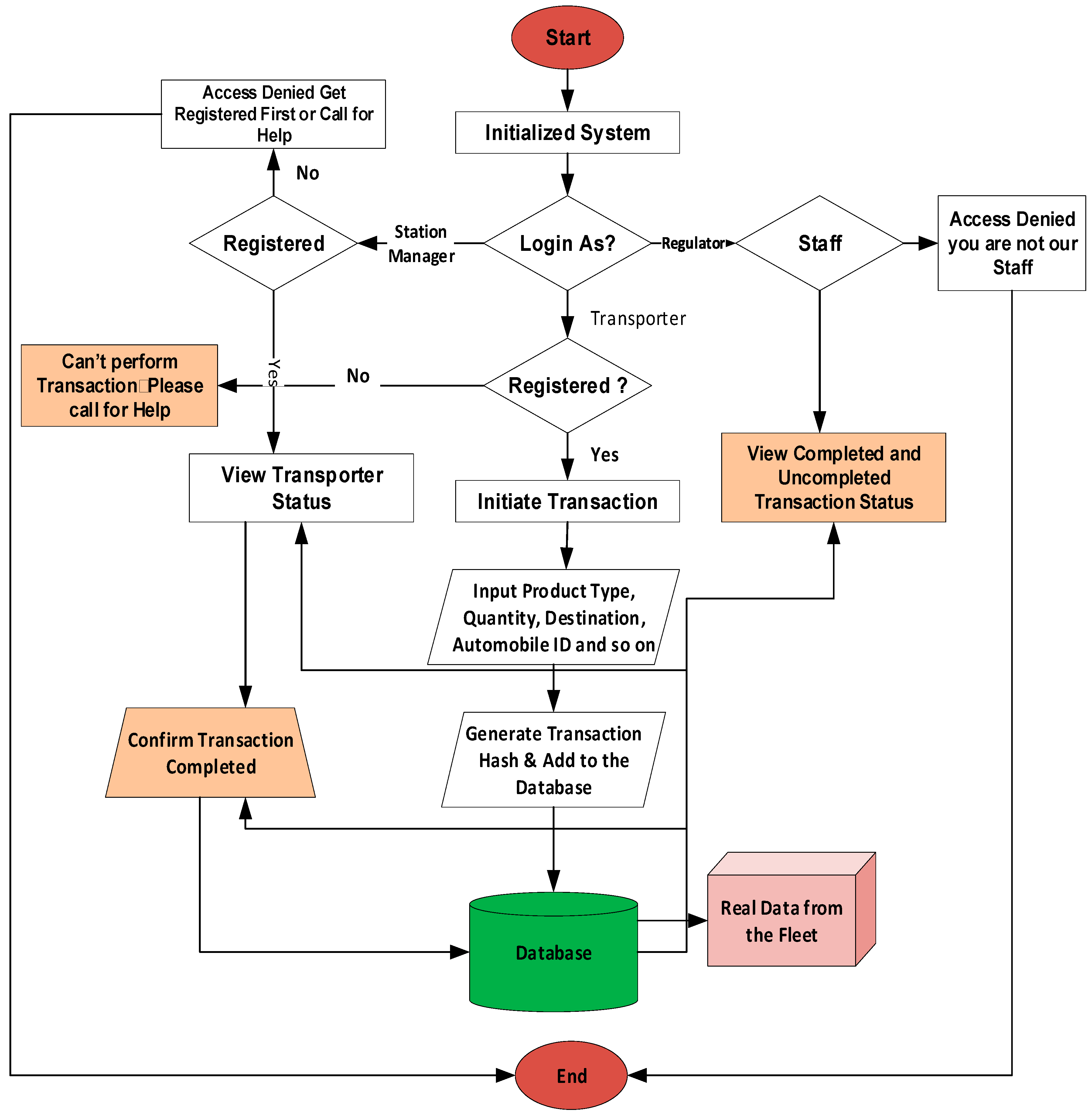
J | Free Full-Text | Crypto Hash Algorithm-Based Blockchain Technology for Managing Decentralized Ledger Database in Oil and Gas Industry

Water | Free Full-Text | Hash-Based Deep Learning Approach for Remote Sensing Satellite Imagery Detection
shows the flow chart of the collision detection algorithm based on a... | Download Scientific Diagram

Detection of deformable body collision using the modified space hash... | Download Scientific Diagram
![PDF] Approach of Tamper Detection for Sensitive Data based on Negotiable Hash Algorithm | Semantic Scholar PDF] Approach of Tamper Detection for Sensitive Data based on Negotiable Hash Algorithm | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/8b154e7d16dddf63b49fe3fa05b7e7337f6824a4/3-Figure1-1.png)