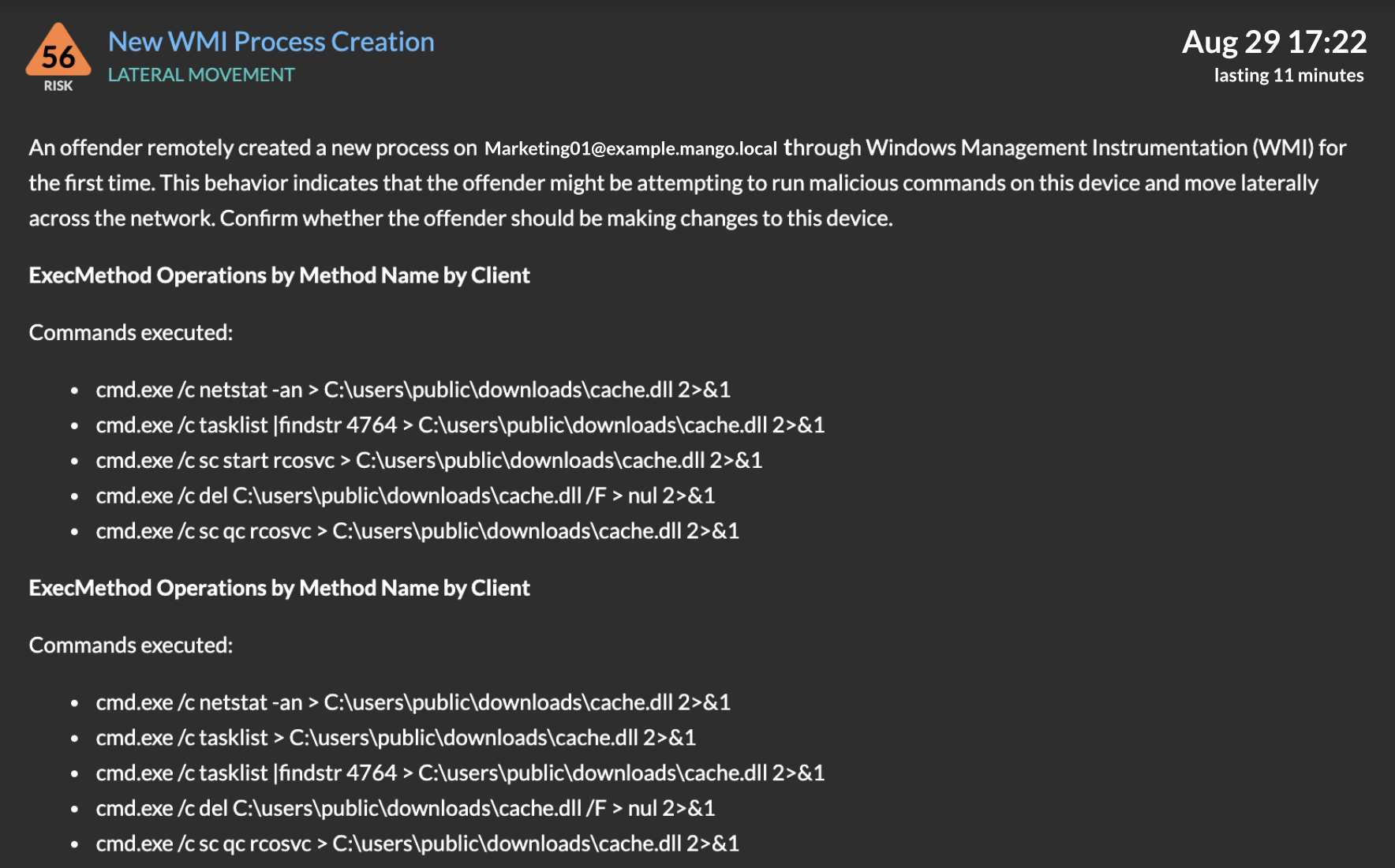
Window-and-face objects detection processes: At a server, following the... | Download Scientific Diagram

SSL-based application detection over decrypted traffic in a sandwich topology | FortiGate / FortiOS 6.4.0

Full disk encrypted drive not booting after putting in decrypt master key check comments : r/ManjaroLinux

Block diagram showing JPEG coding/decoding, encryption/decryption and... | Download Scientific Diagram

Drones | Free Full-Text | A New Image Encryption Algorithm Based on DNA State Machine for UAV Data Encryption

EV2300 Laptop Battery Maintenance Detection Decryption And Unlocking Tool, Monitor The Internal Data Status Of The Battery|Industrial Computer & Accessories| - AliExpress

Encrypting or Decrypting a Large Amount of Data_Data Encryption Workshop_Best Practices_Key Management_Using KMS to Encrypt Offline Data_Huawei Cloud



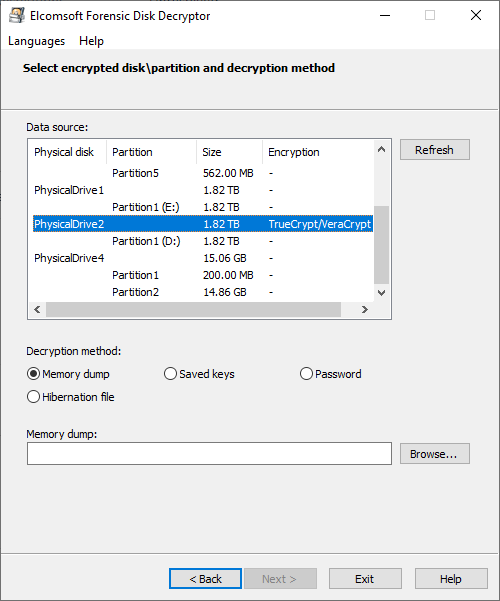


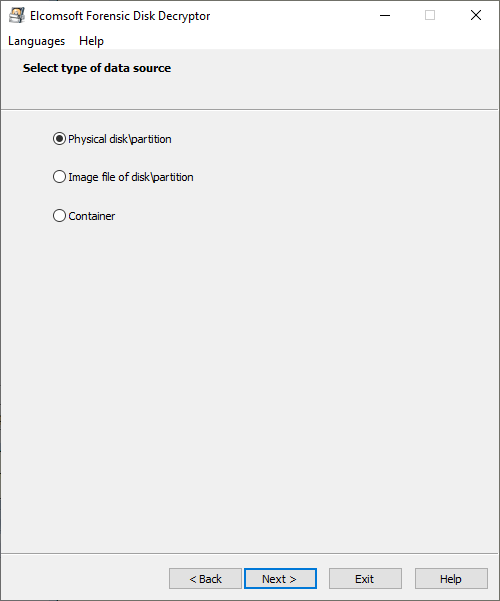
![Eyesight to the Blind – SSL Decryption for Network Monitoring [Updated 2019] | Infosec Resources Eyesight to the Blind – SSL Decryption for Network Monitoring [Updated 2019] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/062111_1907_Eyesighttot1.png)