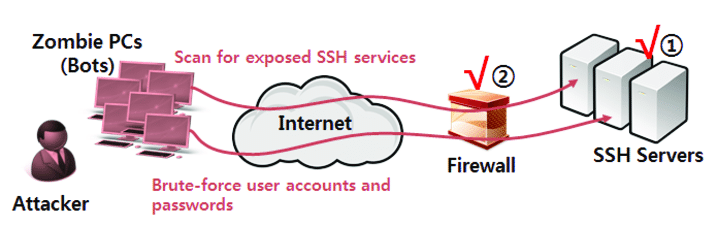
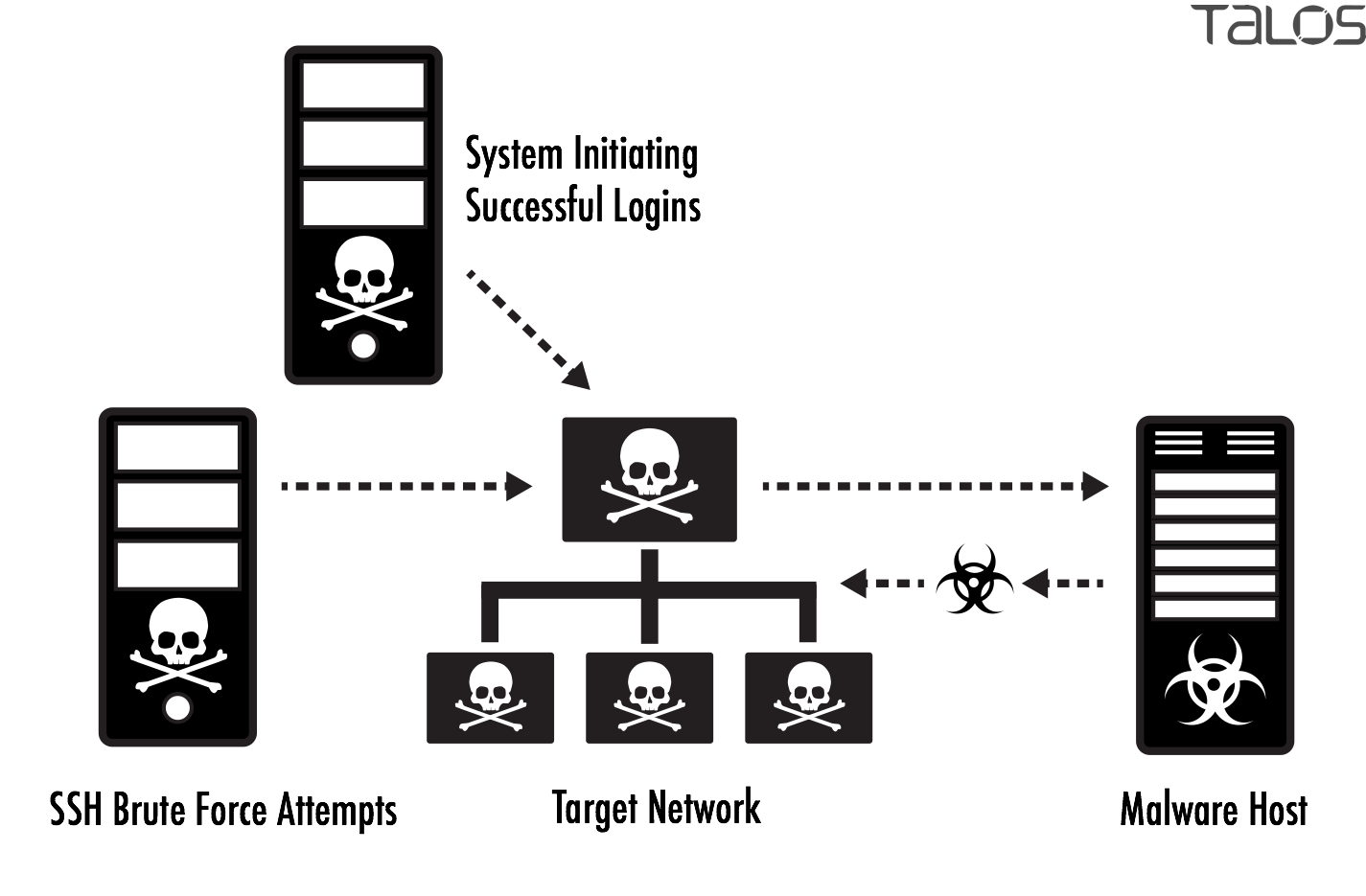
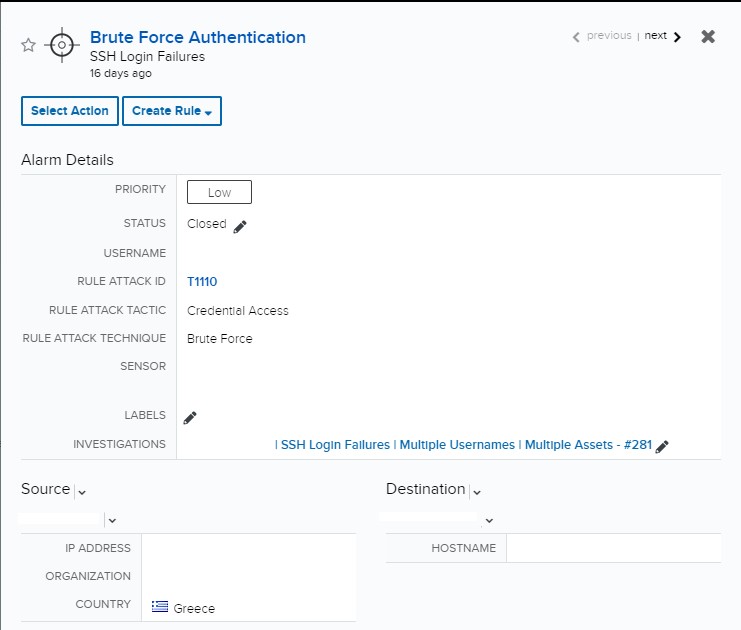
A four levels correlation tree to detect a brute force attack against... | Download Scientific Diagram

Automation to Block Brute-force Attacked IP detected by Microsoft Defender for Cloud - Microsoft Community Hub
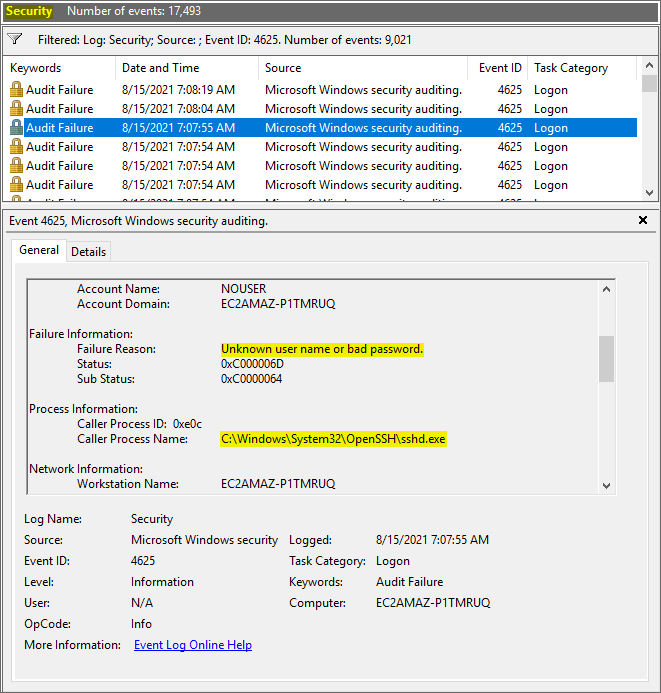
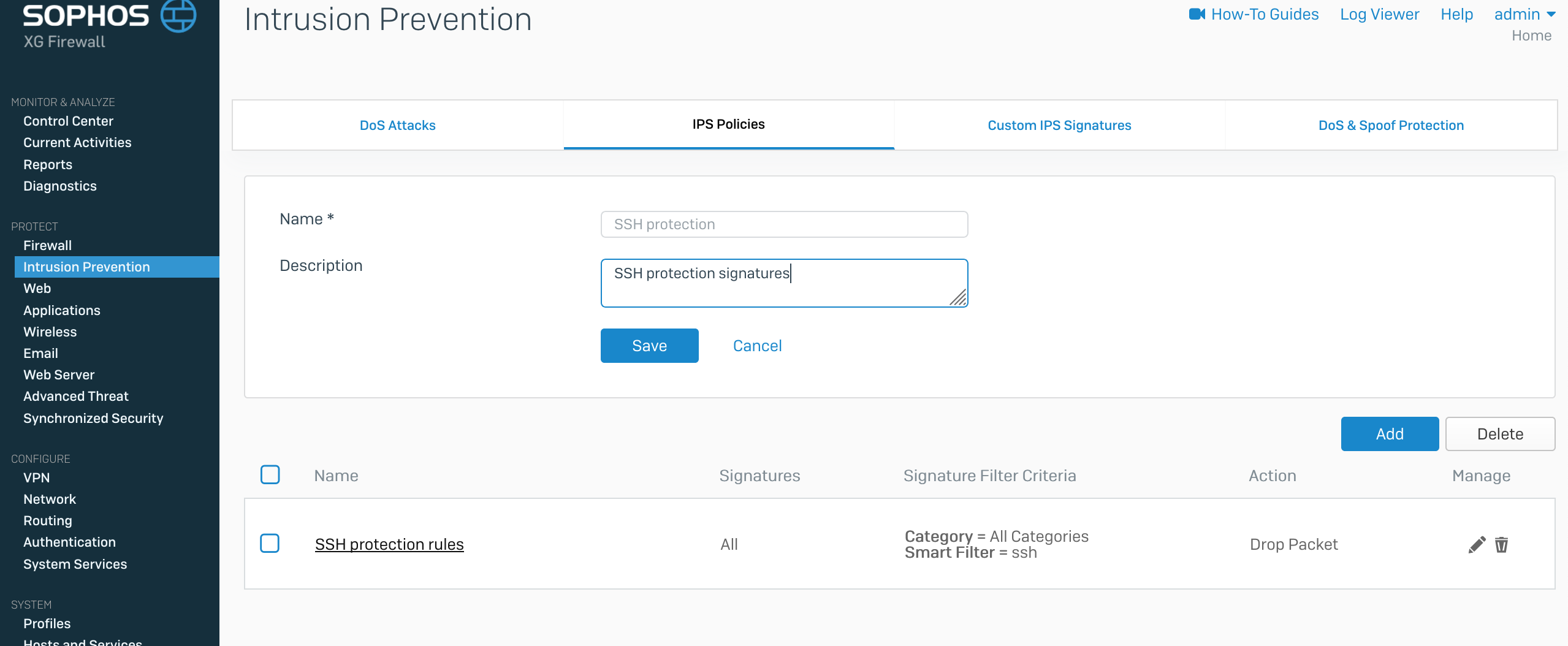
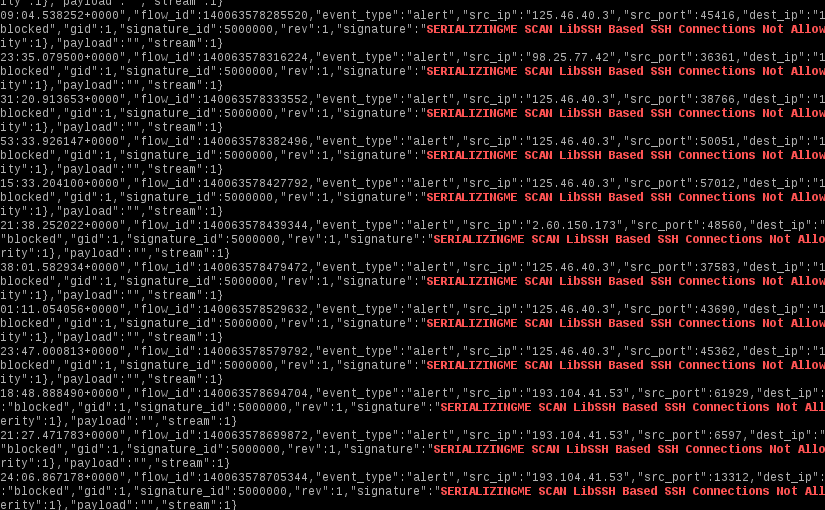
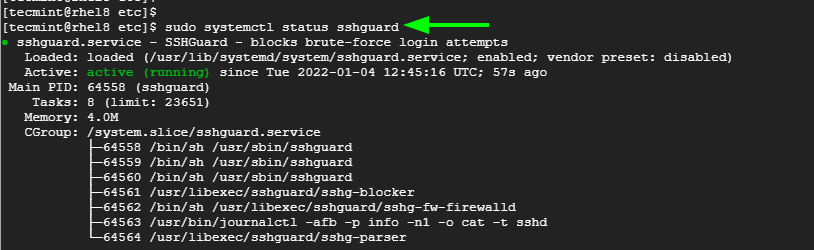
OpenSSH Brute-Force Protection - How to stop brute-force attacks on SSH protocol on Windows. OpenSSH protection on Windows.

Automation to Block Brute-force Attacked IP detected by Microsoft Defender for Cloud - Microsoft Community Hub

Automation to Block Brute-force Attacked IP detected by Microsoft Defender for Cloud - Microsoft Community Hub