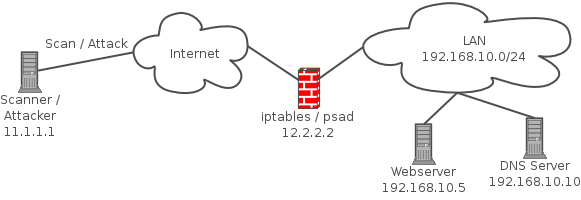
How to block port scan attack using mikrotik firewall !!! Port Scanner (NMAP) Test On Mikrotik. - YouTube
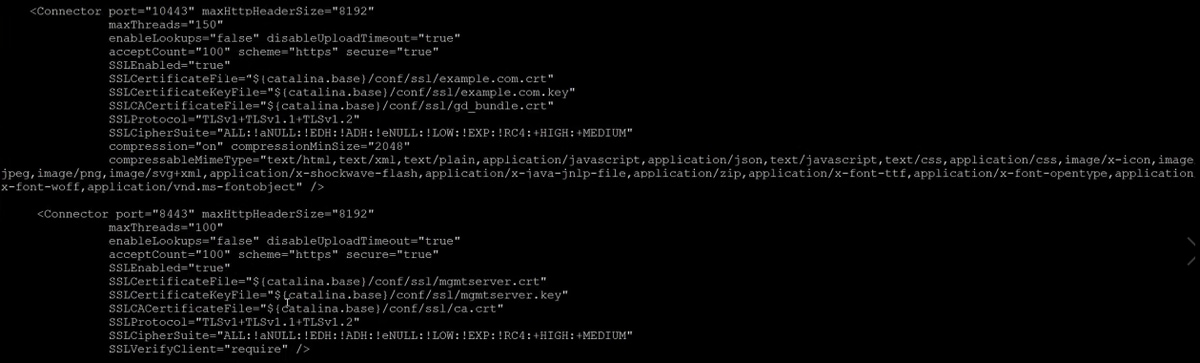
![Testing TLS/SSL configuration using Nmap - Web Penetration Testing with Kali Linux - Third Edition [Book] Testing TLS/SSL configuration using Nmap - Web Penetration Testing with Kali Linux - Third Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781788623377/files/assets/e1a5adf4-46cf-4fcf-a2e0-4029b26c5ecd.png)
Testing TLS/SSL configuration using Nmap - Web Penetration Testing with Kali Linux - Third Edition [Book]

Evading Firewall/IDS during network reconnaissance using nmap | by Prateek Parashar | InfoSec Write-ups

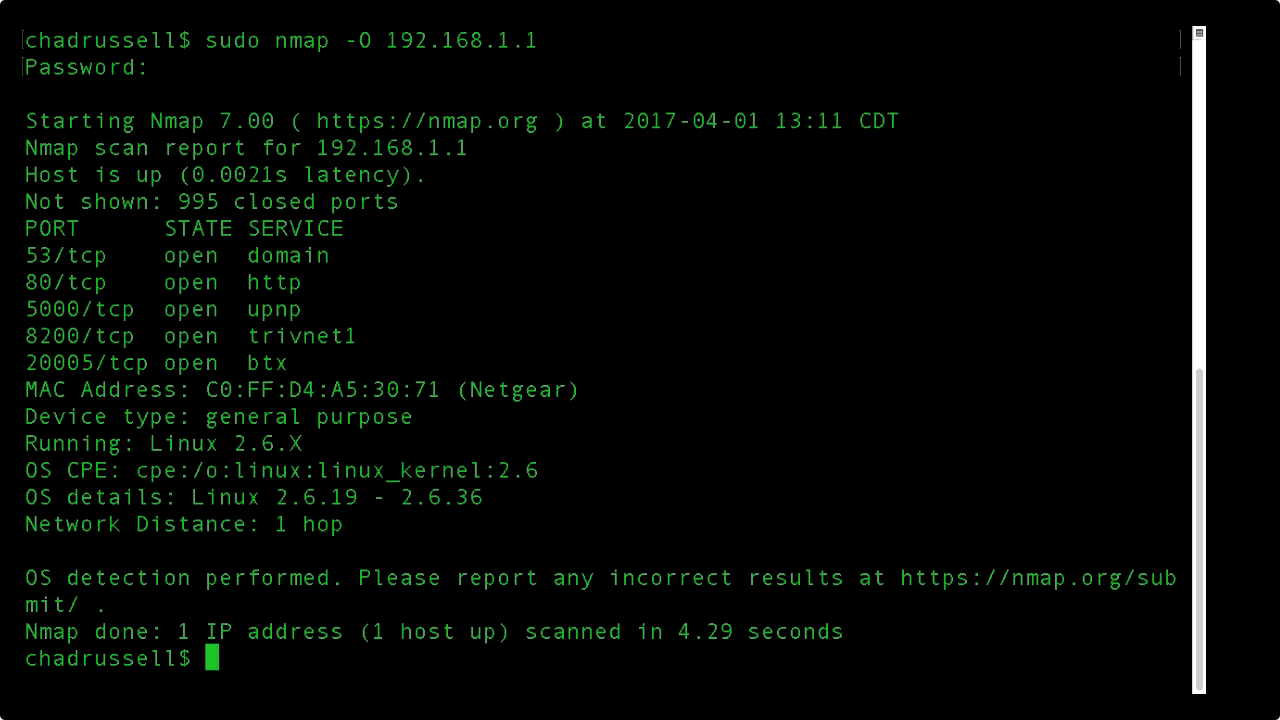
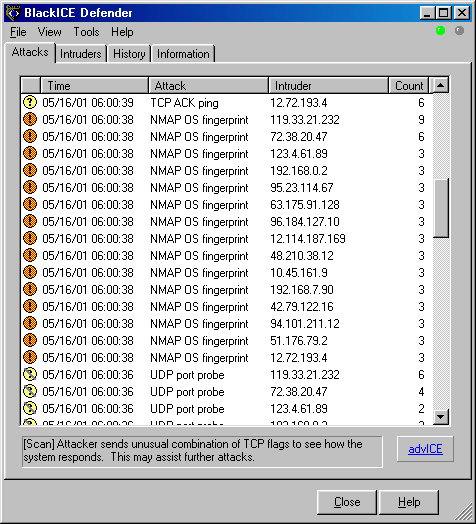




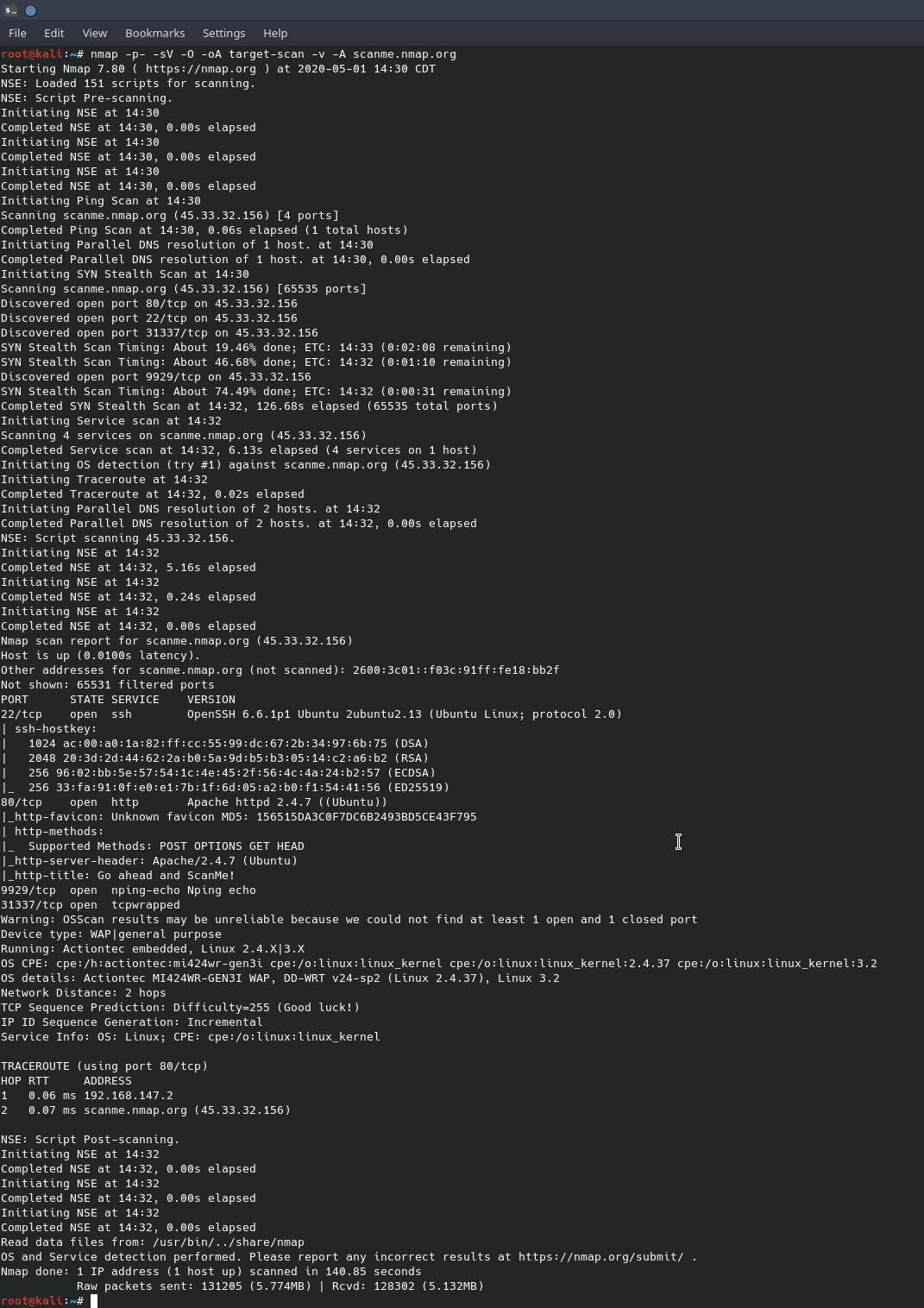
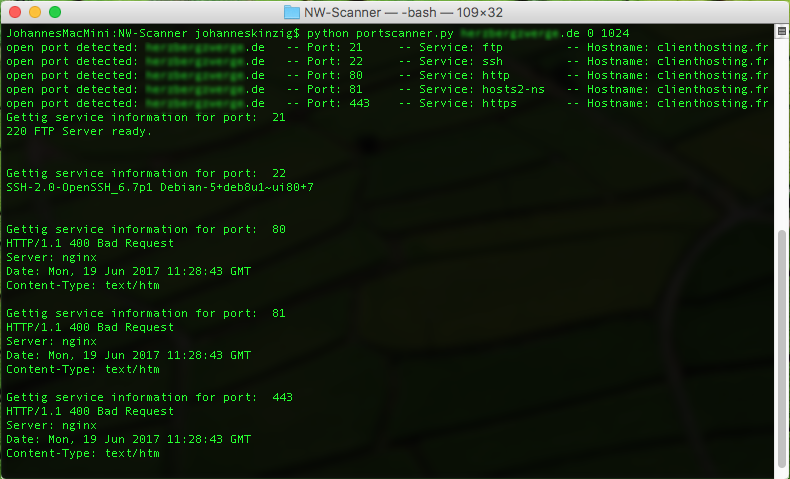


![Nmap evade firewall and scripting [updated 2019] | Infosec Resources Nmap evade firewall and scripting [updated 2019] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/082912_1952_NmapEvadeFi1.jpg)