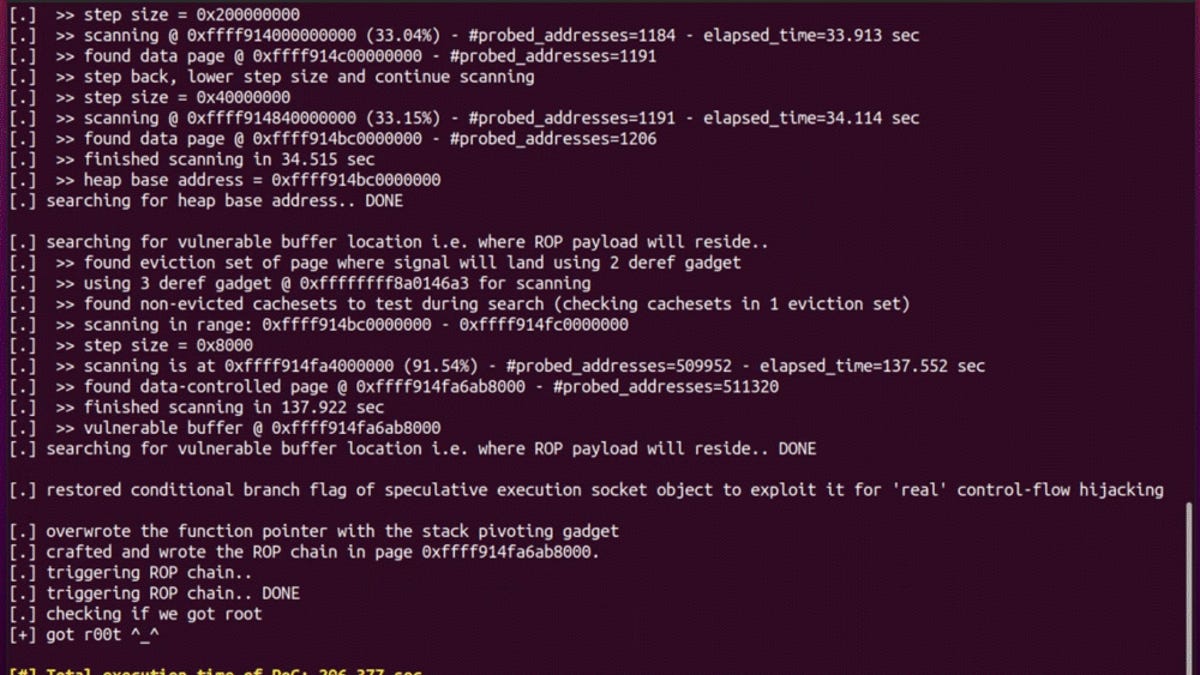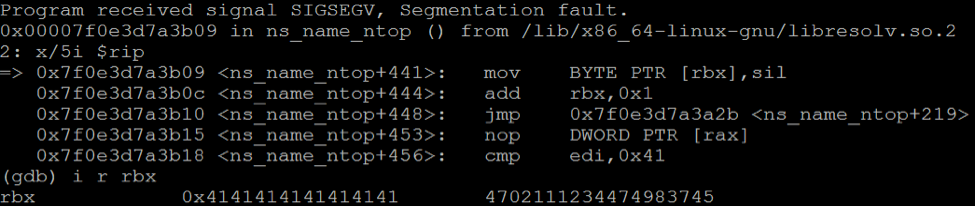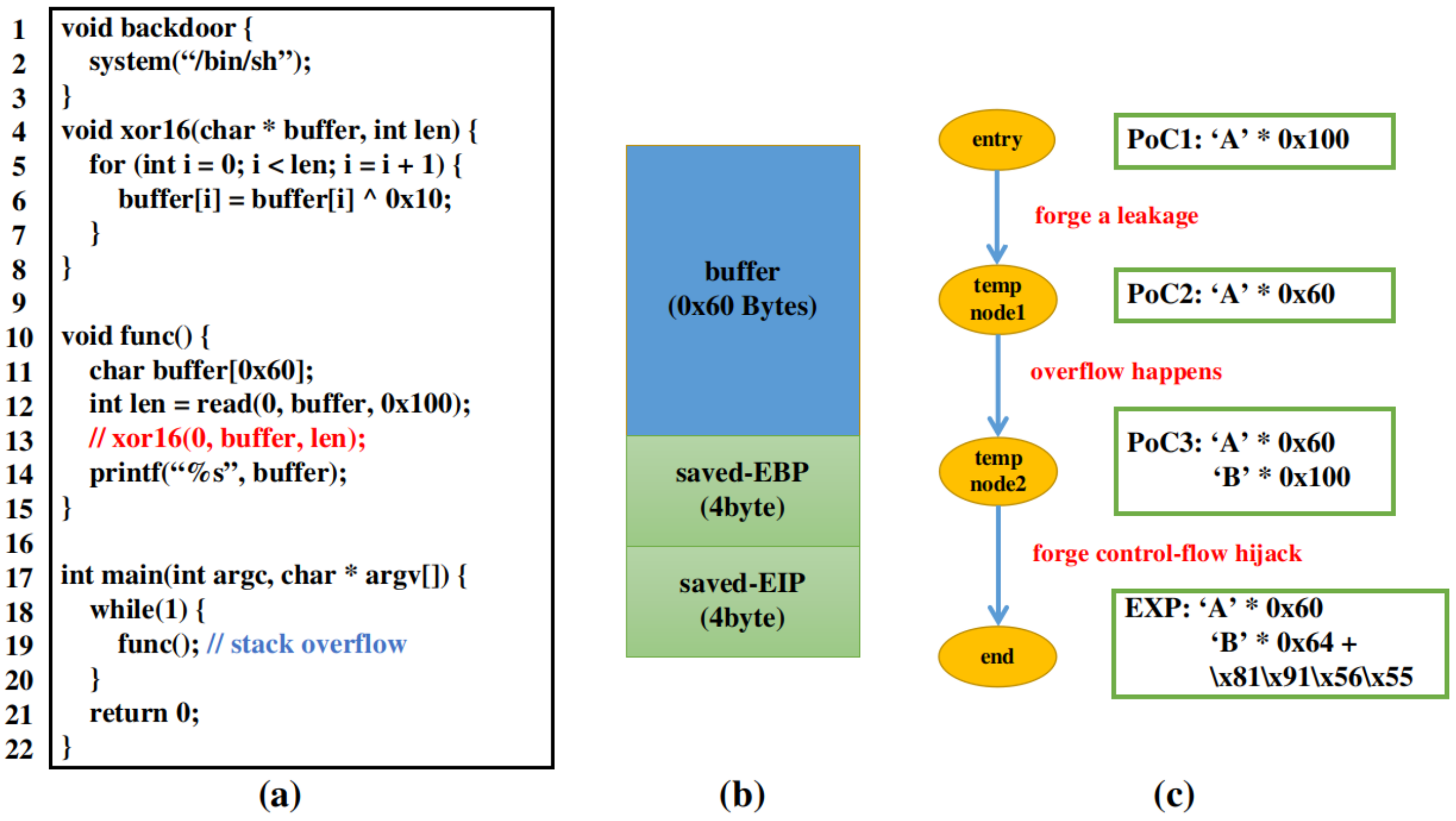
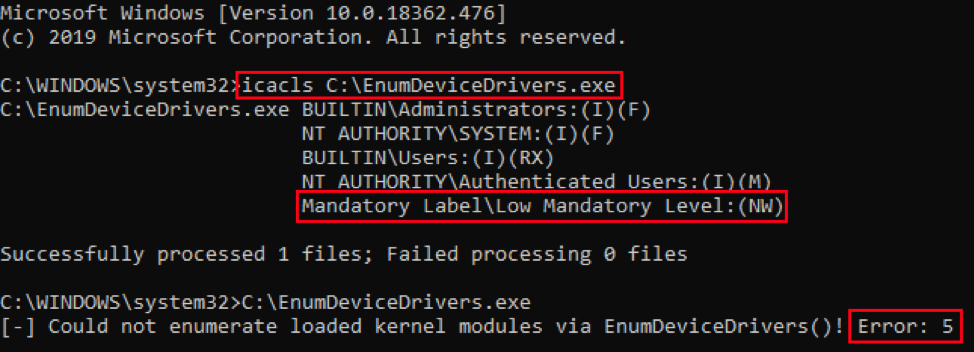
Applied Sciences | Free Full-Text | ExpGen: A 2-Step Vulnerability Exploitability Evaluation Solution for Binary Programs under ASLR Environment
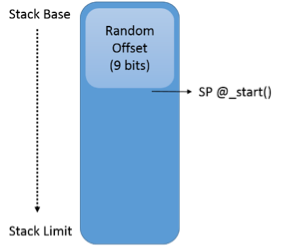
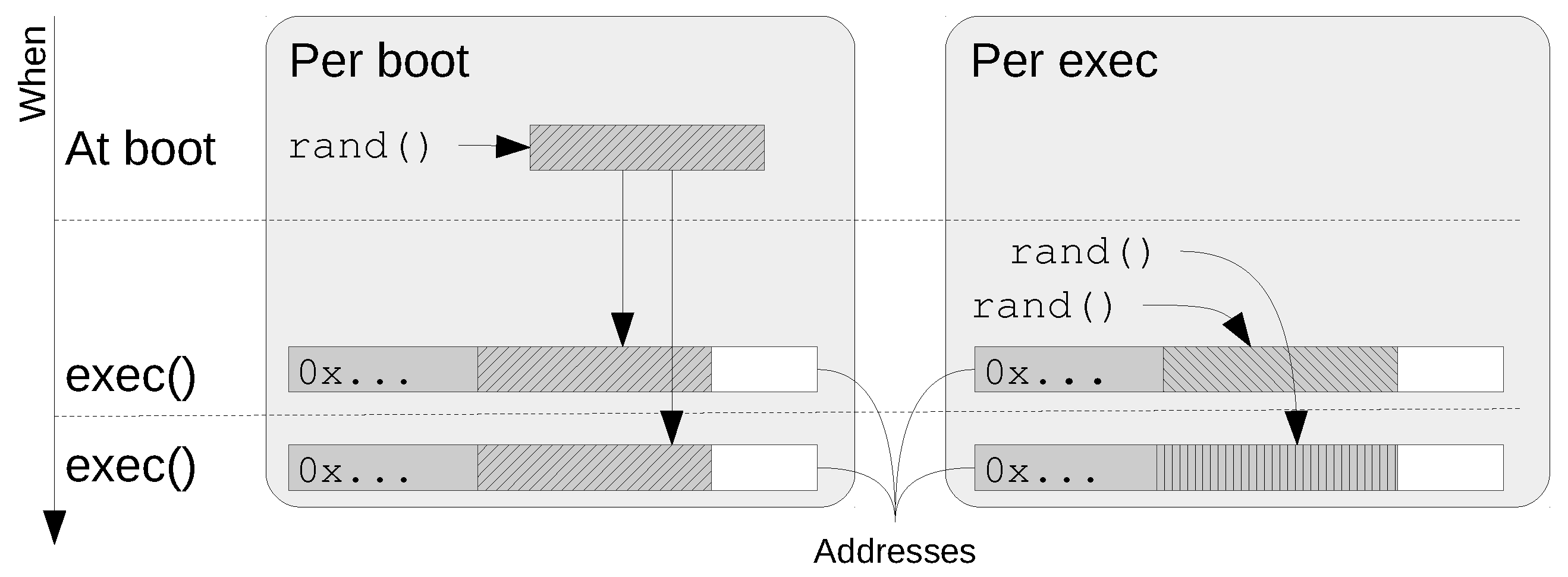
Exploiting Linux and PaX ASLR's weaknesses on 32- and 64-bit systems Black Hat Asia March 29 - April 1, 2016, Singapore






![Aslr On The Line: Practical Cache Attacks On The Mmu [Pdf] | uDocz Aslr On The Line: Practical Cache Attacks On The Mmu [Pdf] | uDocz](https://cdn-v1.udocz-assets.com/uploads/book/cover/21379/21379.jpg)